Safeguard the security of your systems – and success of your business – with expert IT security management services.
Ensuring your systems are protected against cyber threats is vital. Fail to do so, and you risk not only losing out on revenue in the event of a malicious attack, but also permanently damaging your reputation should sensitive data be leaked.

At Box UK we’re experienced in helping clients build effective cyber security monitoring and management capabilities, enabling them to identify, assess and react to threats, maintain all necessary compliance requirements and, ultimately, preserve the information and assets that matter to them most.
Offering clear, practical and actionable guidance, our consultants can work with you to shape a strategy that mitigates risk and safeguards security at every level, while our ongoing monitoring services will alert you to any potential issues or updates, as soon as they arise.
Plus, as a Cyber Essentials-accredited organisation with ISO 27001:2013 certification, you can be confident that the advice we give is in line with both our own Information Security Management System (ISMS) and the very latest industry best practice – helping you stay up-to-date in a constantly-changing environment.
Our cyber security management services
System vulnerability audits
To help us understand your security setup and define a strategy for cyber security risk management, we’ll first conduct an audit of your current ecosystem. Going beyond the standard penetration test – which can often miss critical underlying issues, or deliver misleading results – we’ll use a variety of manual and automated tools and techniques to provide a truly holistic assessment.
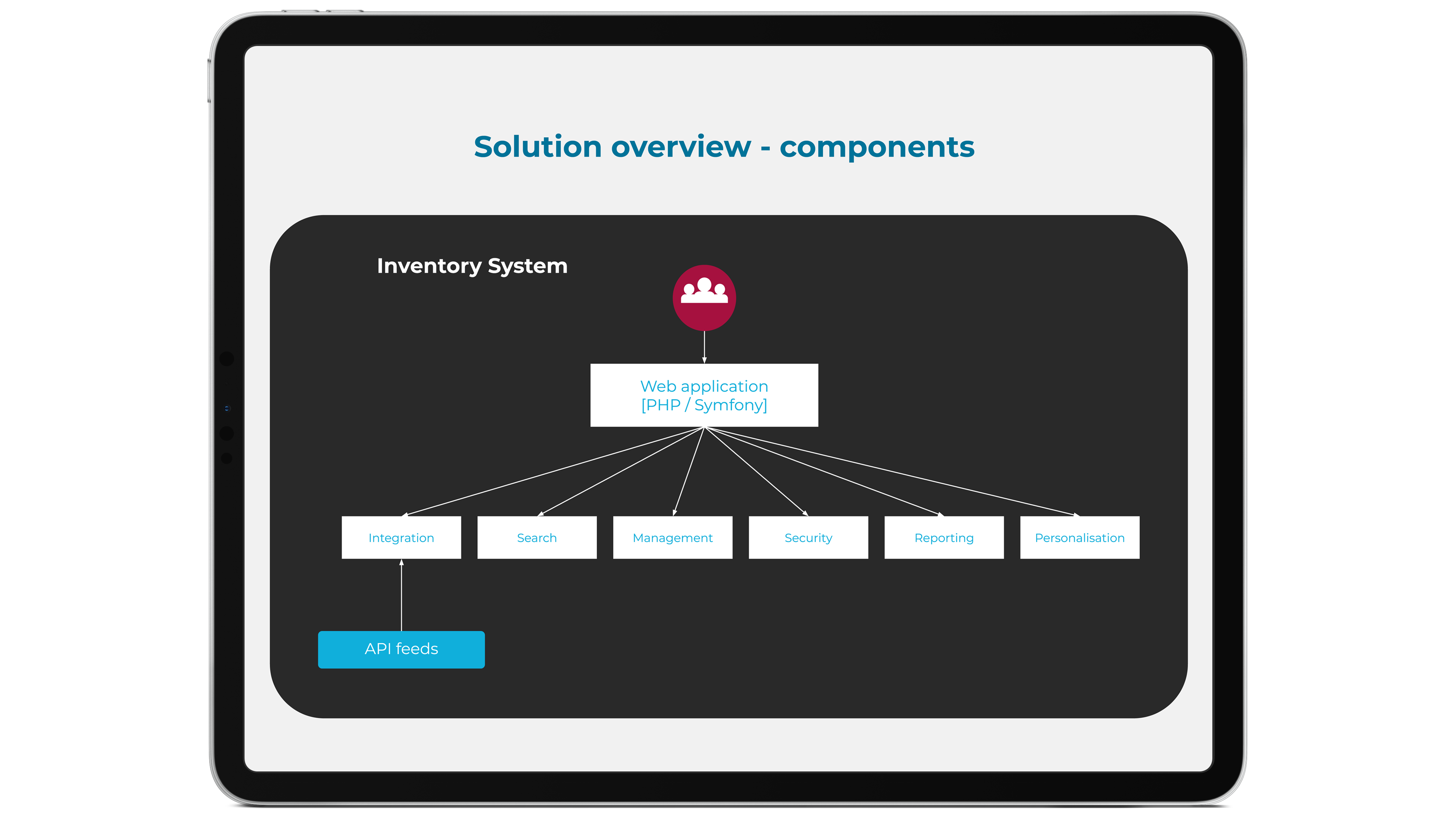
For example, our consultants will perform a detailed analysis of your tech stack, including all integrations, dependencies and data transfer points. And they’ll also seek to understand the wider business context – and the ways in which your team work – through in-depth reviews and interviews.
Our findings will be compiled in a bespoke report that details identified vulnerabilities, prioritised according to their potential to negatively impact your business. Clear, comprehensive and uniquely tailored for you, this is an ideal tool for communication with other stakeholders across the organisation, and can also be used to inform the direction of your future security strategy.
Strategic cyber security consulting
To deliver a security strategy that most effectively supports the smooth and successful running of your business, our consultants will take a collaborative approach to understanding your specific goals and requirements, particular areas of concern (where you’re dealing with sensitive information such as customer data, for example), and any legislation you’re required to comply with.

Combining this insight with the results of our vulnerability audit, we’ll create a tailored strategy to address immediate concerns, ensure your systems are protected for the long-term, and equip your entire team with the knowledge and skills they need to work safely and securely.
We’ll also provide practical recommendations to support you in the implementation of this security management strategy – from the roles and responsibilities needed to govern its rollout and administration, to the documentation and analytics that will enable effective benchmarking and continuous improvement activities.
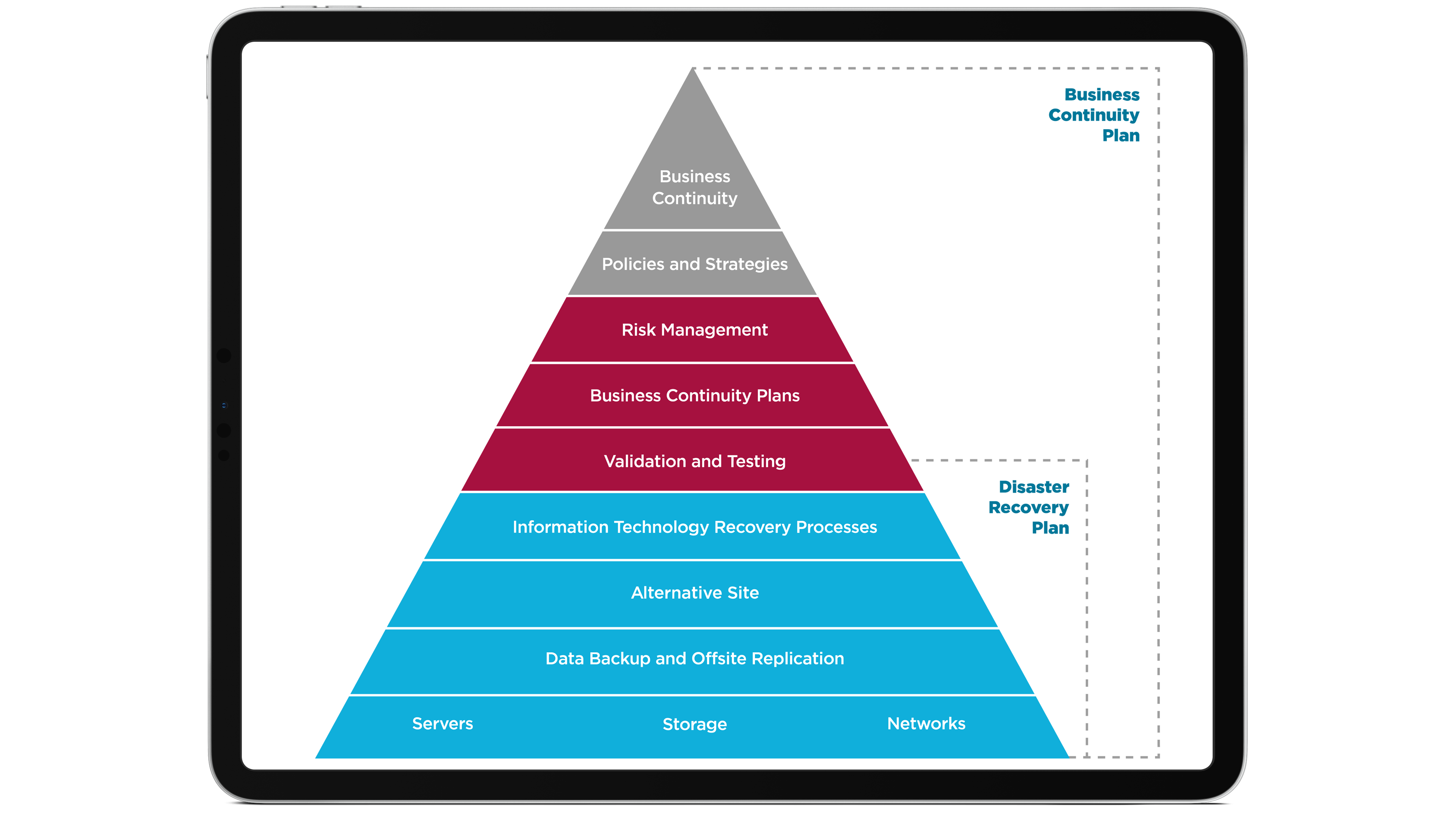
Disaster recovery and business continuity
Even with a strong cyber security strategy in place, incidents can occur that threaten system performance and availability, such as power outages, floods, and fires. We can help you mitigate against these events by advising on an appropriate Disaster Recovery and Business Continuity plan, to minimise the impact of any disruption and enable you to get back up and running as quickly as possible.
After conducting a risk assessment across both your internal and external services, we’ll use the findings to create a clear plan for handling any identified risks. We’ll also provide advice and guidance to ensure this plan is effectively tested, and communicated to all members of your team, so that you can be confident in every aspect of its implementation.
Data recovery
If you’ve already suffered from a cyber security attack or incident that has resulted in the loss of crucial business data, our recovery services can put you back on track with minimal disruption. We can also help you assess the scale of the issue, and take action to restore the information and get your business back up and running as soon as possible.
Ongoing cyber security monitoring
Providing the ultimate levels of coverage and responsiveness, our IT security monitoring services safeguard your ecosystem, taking the pressure off your internal teams and allowing you to focus efforts elsewhere. We’ll embed the latest security tools throughout your systems, focusing on any particularly high-value or high-risk integrations and touchpoints. Custom alerts will ensure you’re made aware of any unusual activity, allowing you to react quickly and address potential threats before they become major breaches.
We’ll also make sure you’re kept up-to-date regarding the tools and technologies underpinning your systems, alerting you to any emerging vulnerabilities and new patches, to keep your systems secure and issue-free for the long-term.
Sodexo
Having conducted a code review for quality-of-life services provider Sodexo that revealed a number of potential security vulnerabilities, upon taking on management of the platform Box UK knew that addressing these was a key consideration.
Taking a proactive approach to effectively diagnosing and communicating risks allowed urgent and high-priority issues to be addressed accordingly. As a result, the upgraded platform is stable, secure and trusted, while also delivering the highest levels of performance and a rich feature set.
ISO 27001:2013
Cyber Essentials Accreditation

